Cyber Security Risk Assessment
Free Cyber Security Risk Status Review and Recommendations.
Understanding your risk exposure is vital to reducing the likelihood and impact of a damaging cyber attack.
We offer customers a FREE cyber risk assessment, one that is designed to cover all of the potential threat landscape and attack surface of their organisation. The starting point for effective cyber security is to review your risk profile and current security posture. Then and only then can you devise a suitable plan for improvements.
The FREE cyber security risk assessment is undertaken during a Microsoft Teams call and normally takes approximately 30 minutes to complete.

If you don't know the risk, you cannot manage it
What do our clients say?
We are experts in managing cyber security projects
Why hire contractors?
Something to think about?
“It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it.”
Stephane Nappo Tweet
Schedule a free cyber security risk assessment
Let’s get the conversation started. Knowing your risk exposure is the first part of your journey to improved cyber security.
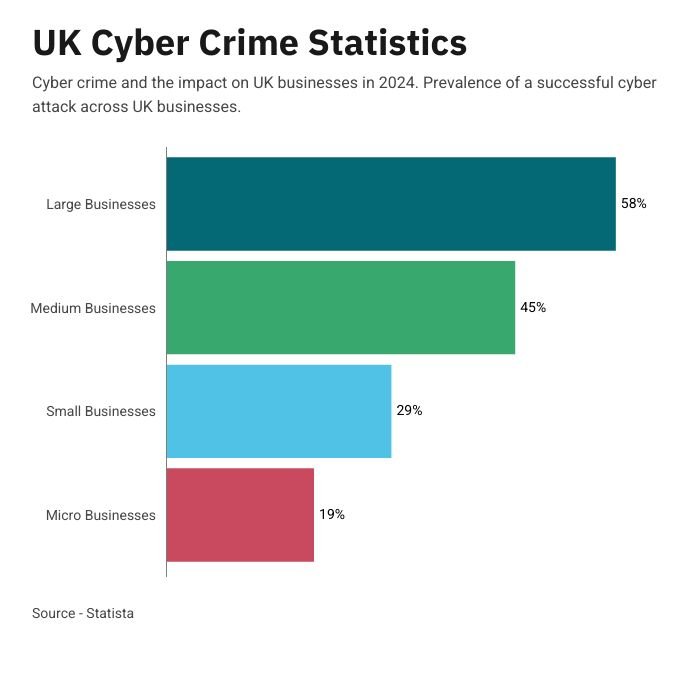
What is the current level of cyber risk?
Over 50% of UK based businesses reported that they were a victim of a cyber attack in the last 12 months. Don’t let your business become another victim.
(Office of National Statistics)
Recent case studies
CISO for Software Business Start Date: April 2022 End Date: In Post Summary One of our certified CISO resources has been the …
Project Delivery Services Start Date: January 2023 End Date: December 2024 Summary One of our senior team members led a large security …
Project Delivery Services Start Date: January 2024 End Date: December 2024 Summary One of our project managers led a large global security …
What's in scope of the assessment?
The following is included in the scope of the risk assessment:
- Security governance
- Security standards, legislation and compliance
- Human resources and security processes
- Training and awareness
- Risk management
- Threat detection and response
- Incident management
- Access controls
- Cloud and on-premise systems
- Vulnerability management
- SOC / SIEM
- Policies and procedures
- Personal data protection
- Email security and management
- Device protection and management
- Back-ups and restoration
- Supplier security management
- Containment and recovery capabilities




